
Please Follow us on Gab, Minds, Telegram, Rumble, GETTR, Truth Social, Twitter
Election Systems and Software (ES&S) have been doing their best to hide Federal and State Election Records from the public. When we started requesting “Audit Logs” and other “Official Election Records” they quickly sent out a bulletin to their customers to not comply with our lawful public records requests for “Official Election Records”. I previously covered this illicit activity last year.
Recently Texas Attorney General Ken Paxton ruled that Texas election administrators were required to provide the “Audit Logs” and “Election Records” that we had been requesting.
In ES&S’ attempt to conceal some of the information requested, they claimed that to disclose some of the information that we had requested would constitute a violation of United States Copyright law.
I personally challenged this exemption under a “Fair Use” exemption to United States Copyright Law to every Texas municipality using ES&S systems to administer elections in Texas. I specifically noted the United States Justice Department position on “Fair Use”.

“…inconceivable that any court would hold such reproduction to constitute infringement.”
ES&S countered with a 27 page legal brief explaining that my particular uses did not meet the legal requirements under “Fair Use”. They also made a stunning admission that completely exposed the extent of the ACTUAL FRAUD that ES&S has been a massive beneficiary of.
On pages 6 - 7 ES&S clearly states that the manuals that we had requested copies of contained default administrator logins and passwords. See image below:
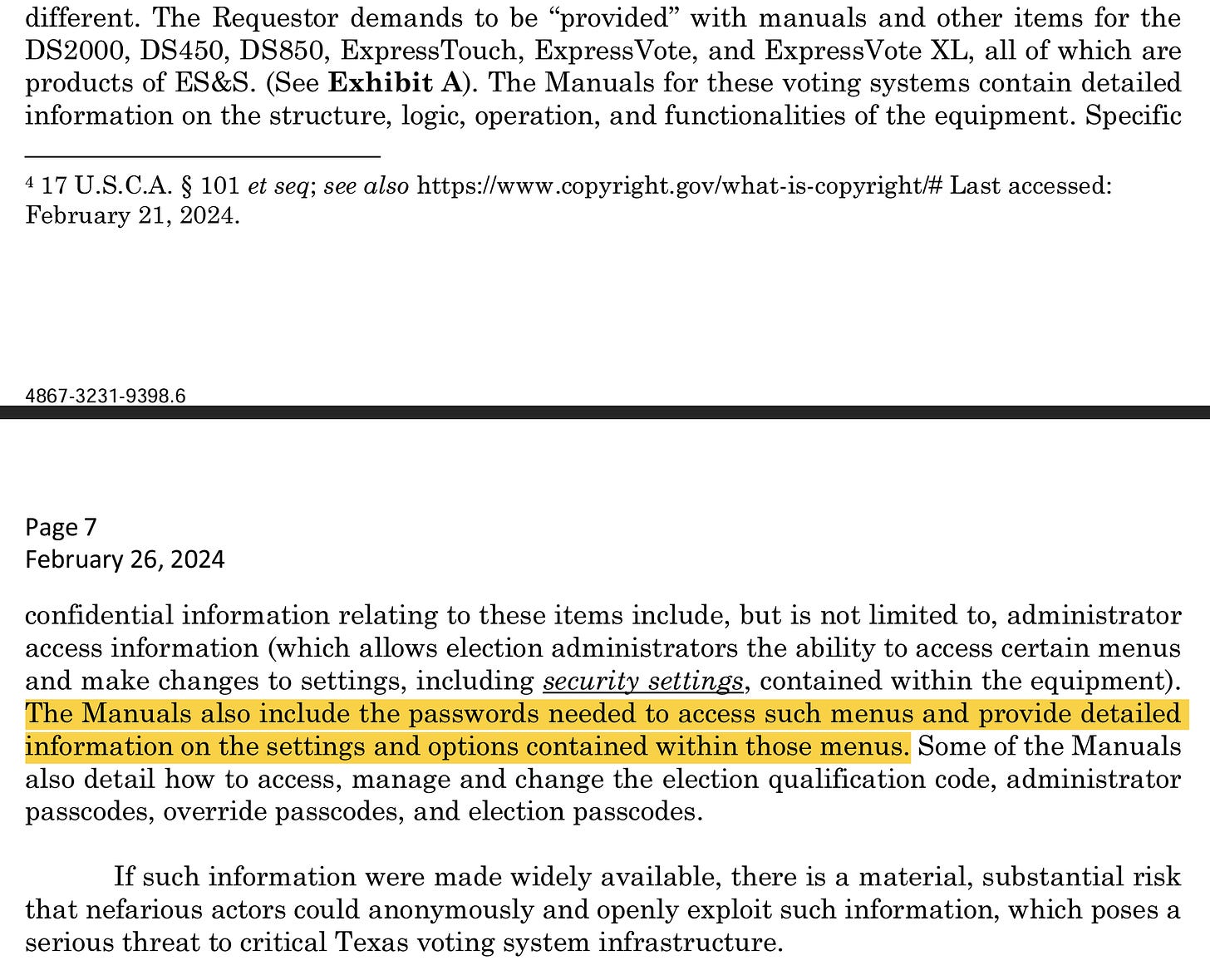
This stunning admission by ES&S to Texas Attorney General Ken Paxton is an admission that ES&S knowingly and willingly violated every cybersecurity protocol and best practice in place today. This is an admission that ES&S has not followed NIST guidelines nor CISA guidelines for electronic systems and software deemed to be “Critical Infrastructure”.
This admission by ES&S certainly does explain why they do not want anyone inspecting the “Machine Configuration Reports”, “Audit Logs” and “Error Logs”. It certainly appears that ES&S’ idea of security best practices are security by obscurity.
The National Institute of Standards and Technology (NIST) provides comprehensive guidelines and best practices for cybersecurity, including the management of system logins and passwords. Based on the principles outlined in NIST's publications such as the NIST Special Publication 800-53 (Security and Privacy Controls for Federal Information Systems and Organizations) and NIST Special Publication 800-63 (Digital Identity Guidelines), we can note key points regarding their stance on handling system logins and passwords.
NIST Guidelines on Password Management:
1. Complexity and Strength: NIST recommends the creation of strong, complex passwords that are resistant to guessing and brute-force attacks. This often involves a combination of letters, numbers, and special characters.
2. Storage and Transmission: NIST advises that passwords should be stored and transmitted securely, using encryption to protect them from interception or unauthorized access.
3. Access Control: NIST emphasizes the need for proper access control measures to ensure that only authorized individuals have access to sensitive information, including login credentials.
4. Password Confidentiality: Maintaining the confidentiality of passwords is a fundamental aspect of NIST's cybersecurity framework. Passwords are considered sensitive information and should be protected accordingly.
How would this relate to publishing generic the same administrator logins and passwords for every ES&S System in use across the world?
Implications for Operator Manuals:
- Listing system logins and passwords directly in operator manuals would likely be considered a violation of NIST's cybersecurity standards and best practices. Such an approach would compromise password confidentiality, expose critical systems to potential unauthorized access, and undermine the overall security posture recommended by NIST.
- NIST's guidance would more likely support the secure distribution of credentials through controlled means that ensure access is limited to authorized users only. This could include secure electronic distribution methods, the use of secure password management systems, or direct communication to authorized individuals under strict protocols.
Publishing administrator logins and passwords that are not unique compromises the integrity and security of devices, especially those deemed critical infrastructure, for several reasons:
1. Elimination of Access Control: One of the fundamental principles of cybersecurity is access control, which ensures that only authorized users can access certain information or systems. By publishing generic administrator logins and passwords, this principle is violated. It allows anyone with access to the information to potentially gain administrative access to the system, bypassing any form of identity verification or access management.
2. Increased Vulnerability to Unauthorized Access: Generic and publicly known credentials significantly lower the barrier for unauthorized users to gain access. This could include malicious actors who intend to steal sensitive data, disrupt services, or inject malicious code into critical infrastructure systems.
3. Facilitation of Insider Threats: Even within organizations, not all individuals should have access to all systems or data. Publishing generic admin credentials internally could facilitate unauthorized access by insiders, increasing the risk of data breaches or sabotage from within.
4. Undermining Multi-Factor Authentication (MFA): Critical systems often employ MFA to enhance security by requiring more than one form of verification before granting access. If generic admin logins and passwords are known, the effectiveness of MFA is compromised, as possession of these credentials could allow an attacker to bypass or manipulate the additional authentication steps.
5. Difficulty in Auditing and Accountability: Tracking who has accessed a system and what changes they have made is crucial for security and compliance, especially in critical infrastructure environments. Generic credentials make it impossible to accurately audit system access and activity since multiple individuals could be using the same login, thereby eroding accountability and hindering the investigation of security incidents.
6. Compliance Violations: Many regulations and standards governing critical infrastructure mandate strict controls over access to systems and data. Publishing generic administrator credentials could violate these requirements, potentially leading to legal and financial consequences, in addition to compromising security.
7. Erosion of Public Trust: For technologies and systems designated as critical infrastructure, public trust is paramount. The knowledge that such systems are protected by generic and publicly known credentials could erode trust in the managing organization's ability to safeguard its systems and, by extension, the public's safety and well-being.
The practice of publishing generic administrator logins and passwords for critical infrastructure technologies fundamentally undermines the security and integrity of these devices. It contravenes established cybersecurity principles and best practices, potentially exposing critical systems to a wide array of cyber threats. Organizations responsible for managing critical infrastructure must adhere to stringent cybersecurity practices, including the secure management of access credentials, to protect against unauthorized access and maintain the resilience of these essential services.
Does this help explain better why ES&S and the “(S)election administrators” across America are so intent to hide their neglect of duty, incompetence or outright removal of the consent of the governed?
How do you think that this could be related to what we identified in Maryland last week?
It certainly help explain the “Clerical Errors” seen in elections in Pennsylvania during the November election there last year.
It’s time to start asking some critical questions…
Under Texas law, fraudulent practices encompass a range of deceptive acts intended to gain an unfair advantage or to harm another party. If an electronic election system manufacturer were to try to conceal the use of generic administrator logins and passwords as a standard practice, it could potentially be scrutinized under several legal frameworks for fraudulent practices, especially if this concealment led to misrepresentations or false claims about the security of their systems. Key considerations include:
1. Deceptive Trade Practices: The Texas Deceptive Trade Practices-Consumer Protection Act (DTPA) prohibits false, misleading, or deceptive business practices, breach of warranty, and unconscionable actions. If a manufacturer knowingly conceals that their security practices include the use of generic logins and passwords, thereby misrepresenting the security of their systems to election officials or the public, this could constitute a deceptive trade practice.
2. Fraud: Under Texas law, fraud involves intentional misrepresentations or omissions of material facts that another party relies upon, to their detriment. Concealing the use of generic logins and passwords, especially if the manufacturer asserts their systems meet certain security standards, could be considered fraud if entities purchasing the systems relied on these assertions when making their decision.
3. Breach of Contract: If the manufacturer has entered into contracts with state or local governments that include stipulations about the security features of the voting systems, concealing the use of generic logins and passwords could also constitute a breach of contract, especially if the contracts require adherence to specific cybersecurity practices.
If this is occuring in Texas, Florida, Maryland, Wisconsin, and Pennsylvania do you think that this occurred anywhere else ES&S has their systems in place?
ES&S believes that their commercial interests far outweigh that of the “PUBLIC INTEREST” in knowing that their elections are free, fair and transparent.
ES&S is also very keen to keep hidden from public view how millions of voters in elections across the United States of America are routinely having their ability to cast ballots and have their votes accurately counted interfered with.
I know that ES&S has been reading what I have been posting and the video interviews that I have been giving as they mentioned it in their brief to Ken Paxton. So I would like to specifically thank Eric Anderson, Vice President & General Counsel for ES&S for helping us make the case that ES&S Systems are not secure and that the United States Election Commission (EAC) should revoke their approved manufacturer status and the revoke every ES&S system EAC Certification in use today across America.
I would also suggest to Eric Anderson that he review the other articles that I have posted using excerpts and screen shots from the ES&S Manuals that clearly demonstrate how “educational and non commercial my use has been”, how “transformative the use of screenshots have been used to critic and expose how the use of ES&S systems have disenfranchised millions of voters, depriving them of their right to cast ballots and have their votes accurately counted”, how “there has been limited use of their copyright materials and I have not widely distributed their manuals”, and how “the effect of the use upon the potential market for the value of the copyrighted work” is not affected as I am not making a business selling their manuals. In fact, one could argue that my use, review and critic of their copyright works could improve the market value of their work by showing how secure their systems were (if that was actually the case, they proved that they aren’t in their recent brief).
Thank you for reading Immutable Truth - Election Integrity. This post is public so feel free to share it.

Any voting system connected to the internet via a modem or network device should not be used to administer elections. We know that they are. ES&S openly admitted that their systems were.

So to recap, ES&S knowingly included passwords and logins in their manuals, that allow for anyone with the login and password to access the systems. ES&S also then built and deployed these systems, with modems and network cards that are connected to the internet.
I strongly suggest that if you should petition your local and state election administrators for hand marked paper ballots, hand counted at the precinct level, one day voting, with voter id and no more vote by mail ballots.
There is a growing movement that is bipartisan that wants to ensure this insanity is stopped once and for all. One such organization is the Coalition For Real Elections that has reasonable measures to ensure that every real vote by every real voter is counted accurately.
If you value the journalism that I do here please consider sharing my work with the people in your circle of influence and with your (S)elected officials and let them know that this is the removal of the consent of the governed and is not acceptable.
Subscribe to our evening newsletter to stay informed during these challenging times!!
My husband and I have had absentee ballots for ever. We have them now for our Arizona primary. However, not sure exactly how to vote this time around, whether to drop them off early or wait until the end or vote in person, I guess turning in our ballots at the same time, but just don't trust who we turn them into. So frustrating.
Best to vote at the polls on election day. Early voting tells the bad actors how much they need to cheat to win. (That's right. They have access to that data.)
They are also able to run lists of who has not voted, so they can usurp your vote. Many people showed up at the polls in 2020 only to be told they had “already voted.”
Robert is correct, the voter rolls make new cloned voters that cheaters use to bring up their loser candidates rolls. When you vote early, you're giving them notice they need to deploy a clone. The only way to prevent them from deploying enough clones is to vote Day OF. Bring your mail in ballot with you when you vote in person and destroy it however they suggest.
Can you imagine the level of fear and panic in the administration offices of ES&S and the other vote machine companies.
We seem to cover some of the same ground. Some of the language in that open records letter comes from a project that I did a while back. I beat them on every issue they raised except copy write. That law in relation to public information law is not well developed. Hart was involved also.
The open record letter is actually written by a low level staff attorney and doesn't carry a huge amount of weight. they aren't supposed to be used as precedent, but it tends to happen anyway.
Your work is well researched and documented. I wish I wrote as well.
I think Es&S is lying about the passwords. I have a partial set of manuals and it does not contain them it would be a truly stupid thing to do if they did. they do tell of the process to change them as best i recall, but that isn't something that's terribly difficult.
.
Lastly Audit logs should have been available in Texas all along. The SoS has specifics on their availability in the Texas Administrative code.
Chris - ES&S admitted in a public training in Minnehaha County that they have all the user names and passwords for the election officials. Please contact me - the COA lead for SD. Thank you!