
Please Follow us on Gab, Parler, Minds, Telegram

Patrick ByrneA concerned citizen who has been hunting the oligarchy and Deep State since 2004.
(Warning to reader: this introduction is choppy. I am just trying to accommodate the public by getting blocks of my narrative up quickly. When I finally weave them all into one story I will improve the writing, add more links etc. Last edited/augmented 1/26 1 PM Eastern).
In July, 2020 I had surgery on my spinal chord, as one of my legs had gone paralyzed over the early months of the pandemic. On the last day of July, 2020 a dear friend of mine from Montana, a stolid, Native American fellow several years my junior, visited me at my home in Utah to check on my health. He told me that there was a group of people, some ex-federal some not, some cyber-experts and some of various other expertise, who were organizing on the subject of election fraud. My friend was adamant that I get involved and help them. My friend was quite a squared-away individual, and I took his advice and requests seriously.
The next day, August 1, my friend died in a plane crash. Though the coincidence is troubling, I looked into it personally (I am a multi-engine instrument land and seaplane pilot), and it does seem to me to have been the error of his instructor, who flew the plane into a Montana box canyon without the power to climb out.
At my friend’s funeral I met some of the people he had described. A sober, quiet man with a FEMA background and a deep knowledge of biowarfare; a retired Army Colonel with a background in Military Intelligence including psyops; other men and women with backgrounds in everything from law enforcement to cyber operations in military contexts and in support of law enforcement (such as, most recently, operating against human trafficking rings in the Southwest) to the study of reverse-engineering mass election fraud. It turned out that there had been some irregularities in the Dallas 2018 election that had spawned a network of cyber-enthusiasts on election fraud, and that had spawned a broader network. They were convinced that industrial scale election fraud was possible, and on its way. Soon some key players were dropping through and seeing me in Utah, and I, recovering from surgery, was moving around to meet them elsewhere.
I am now going to write of, “white hat hackers”. I should make clear that I am referring to people who not only follow the law, they generally operate under authority and direction of law enforcement, or under contract with law enforcement at state and federal levels. There is a certification for working in the field of cyber-forensics, a certification that means you can crack open and image hard drives, perform forensics on them, swear out affidavits, and produce work that is admissible in court. Sometimes they are used by law enforcement in offensive cybermissions (e.g., taking down a child trafficking/porn ring). The “white hat hackers” of whom I now write are people with such skill sets, but who operate on the side of the law under contract to law enforcement doing things law enforcement needs done but which are generally beyond the in-house capabilities of law enforcement.
Over the next couple of months I was introduced by these white hat hackers to the security vulnerabilities of the technology used in election equipment. Vulnerabilities such as slots in a motherboard that should be soldered shut but which are open (meaning anyone who can slip a chip into that slot for a few seconds can compromise the machine forever). R232 ports giving any technician who plugs-in root level access without a password (thus again compromising the machine forever). Strange violations of good computer science practice, such as an oddly-architected database within the machine, with three different layers but without integrity among the layers. Audit logs that were editable by precinct administrators (making them not “audit logs” at all), and lacking in fixed numbering systems that could reveal tampering.
I asked the white hat hackers involved who were walking me through these points of porous security to me to rate the security, on a scale of 1-10, of these systems. Their considered answer: “2, maybe a 1”.
Let me point out that a year ago, this was not considered a partisan issue. We all wanted elections that were fair, free, and transparent.
Here is a fine 4 minute video and story from the 2018 New York Times:
“I Hacked an Election. So Can the Russians”

“(“All cybersecurity experts who have given electronic voting machines any thought agree. These machines have got to go… the electronic voting machines Americans got to solve the problem of voting integrity … turned out to be an awful idea. That’s because people like me can hack them all too easily. I’m a computer scientist who has hacked a lot of electronic voting machines… Imagine what the Russians and North Koreans can do… Our highly computerized election infrastructure is vulnerable to sabotage and even to cyber-attacks.” So wrote the same New York times where now, two years later, even mention of the possibility has become verboten.)
from NBC News, from January 2020: “Online and vulnerable’: Experts find nearly three dozen U.S. voting systems connected to internet“.
Here is CNN in 2019: “Watch this hacker break into a voting machine: At the largest convention of hackers in the world, voting machines were turned inside out as hackers demonstrated how easy it could be to disrupt democracy.”
“Princeton Professor Hacks Dominion Voting Machine in Seven Minutes”
Beyond those kinds of hacks, they began to introduce me to other “hacks” understood in a broader sense. The extraordinary privileges enjoyed by precinct administrators, for example, to drag-and-drop a queue of hundreds of ballots waiting for adjudication (a point confirmed within the machine’s operating handbook). Discussion was had of spikes in offshore packet traffic to certain locations during elections, though the full reasons for that were not yet fully understood. One technique that was explained to me before the election, ended up being the subject of a Gateway Pundit video after the election:
As the weeks ticked by this late summer and fall I became increasingly conversant with characters who were convinced we were on the edge of a massive election steal. They had meetings arranged with DHS in their state, and their briefings were taken at least twice in September by DHS and propelled up the chain of command…. only to be killed from Washington. In particular, a portion of DHS called CISA (“Cybsecurity & Infrastructure Security Agency”) put the kibosh on further meetings. This was odd because election security is within their mandate: one might have thought they might be interested. And let me remind the reader, this was not just a ragtag bunch of misfits: these were people with extensive federal backgrounds, with all kinds of experiences and certifications in matters cyber.
Then November 3, the night of the election, everything they had been predicting to me would happen, happened. I am not going to make this essay a full account of the steal: I want to get on with the history. So for fuller research one should go read Sidney Powell’s four briefs to SCOTUS, which come with all sorts of appended material and affadavits. For now, let me confine myself to a brief gloss of the oddities that stacked up.
Ask your local political science professor to explain why it is the case that to steal the national election one does not need, “widespread election fraud”. If the professor is honest, you will hear, “Because instead of widespread election fraud, it only takes deep election fraud in five cities to flip the swing states they are in, to thereby flip the electoral college, and to thereby steal the election nationally. Those cities are Atlanta, Philadelphia, Detroit, Milwaukee, and Phoenix.”
And what do you, know, on November 3, election night, vote counting in precisely those cities took unprecedented turns. As James Woods put it elegantly, “Since when do they just stop counting votes on election day in America?” Yet that happened in various ways across those cities named (it is hard to remember now, but in early November it seemed strange to everyone that they stopped counting votes on election day, though it has been normalized since). In Atlanta’s State Farm Arena, a “water-main break” forced the evacuation of the vote counting area of the arena: it later turned out to be fake (“BUSTED: Evidence Proves ‘Burst Water Pipe’ In Georgia Was Used As Cover For Secret Vote-Counting“) . In the few hours when the counting was “closed”, hundreds of thousands of votes were pushed through the system. The “water-main break” turned out to be a urinal that had overflowed (“Reported Burst Pipe in Atlanta Ballot-Count Area Was Overflowing Urinal: Investigator“).
In one location, multiple security cameras caught workers grabbing suitcases of ballots out of hiding and feeding them into machines while counting was officially stopped and all others had been shooed from the area.
Some of these cities saw goons muscle observers away from vote counting centers on gobbledygook reasons, while others taped pizza boxes across windows to block poll observers from being able to observe.

In the days after the election the suspicion that untoward things were occurring were ubiquitous. Focus of the suspicion was focused on Dominion Voting (“Dominion Machines Cover Millions of Voters, But Watch How Easy It Is To Rig One of Them” Western Journal, November 13, 2020). However, in my opinion that focus insufficiently appreciates the true nature of the issue of election fraud in the USA, its scope and varieties.
Within days, the cyber teams I was with were coming up with data that showed what had happened in those windows where counting had been “stopped”: hundreds of thousands of ballots had been injected, often running 99.4% and even 100% Biden.
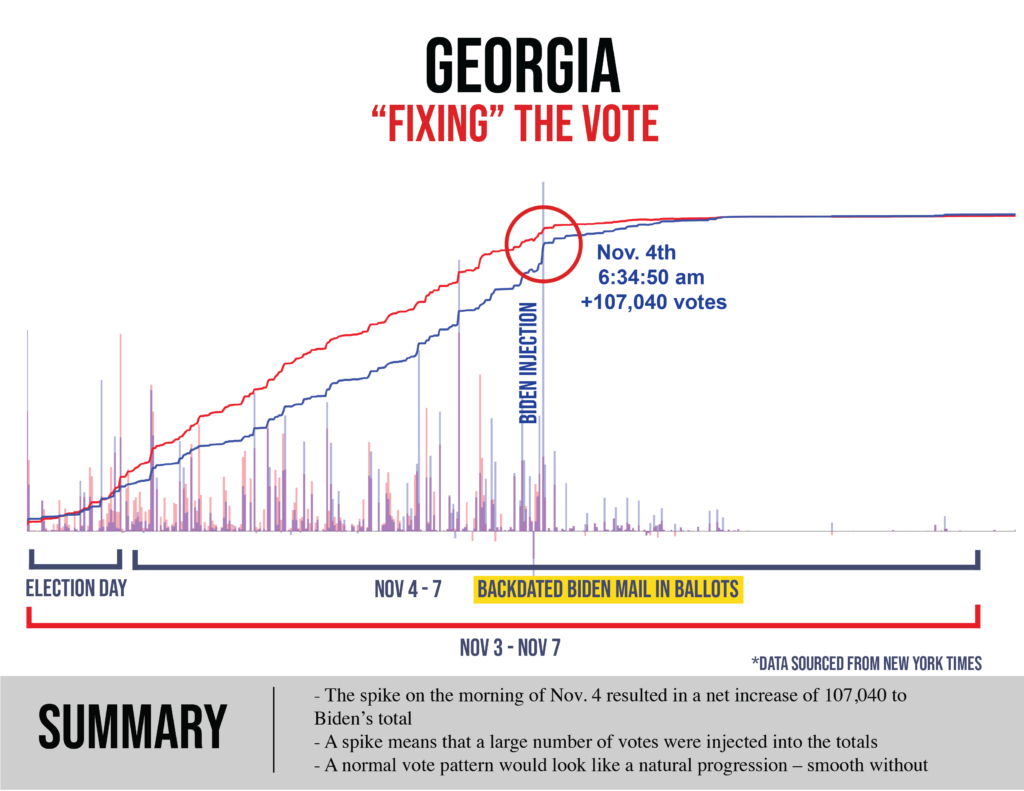
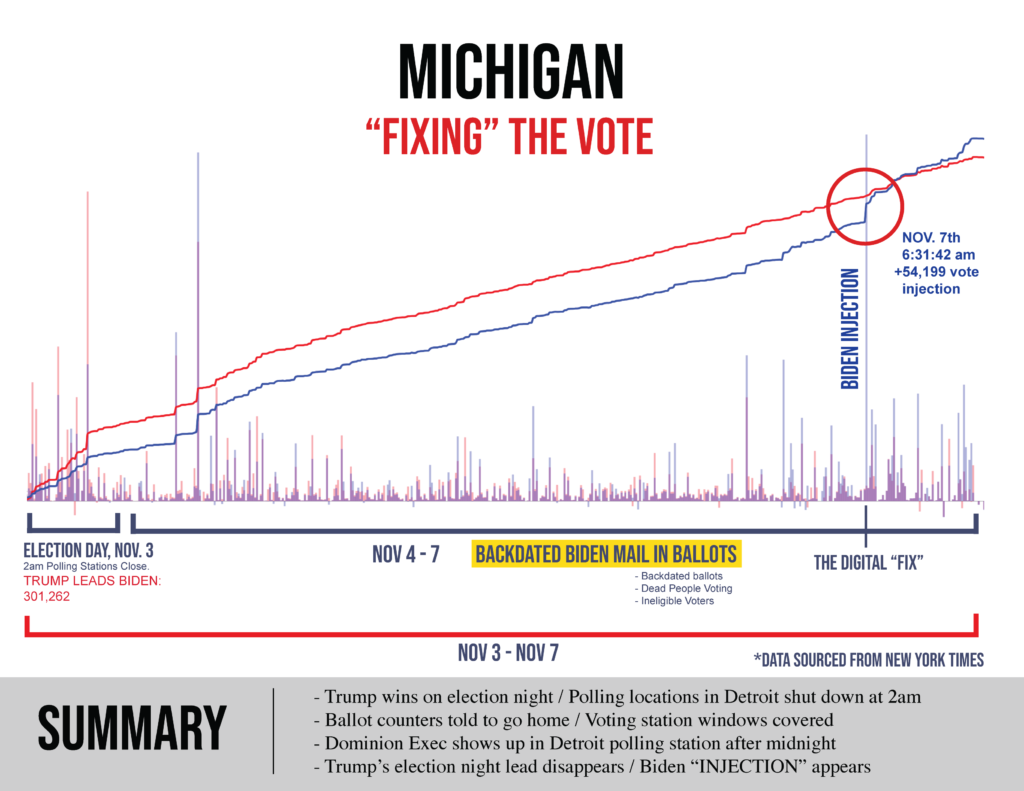
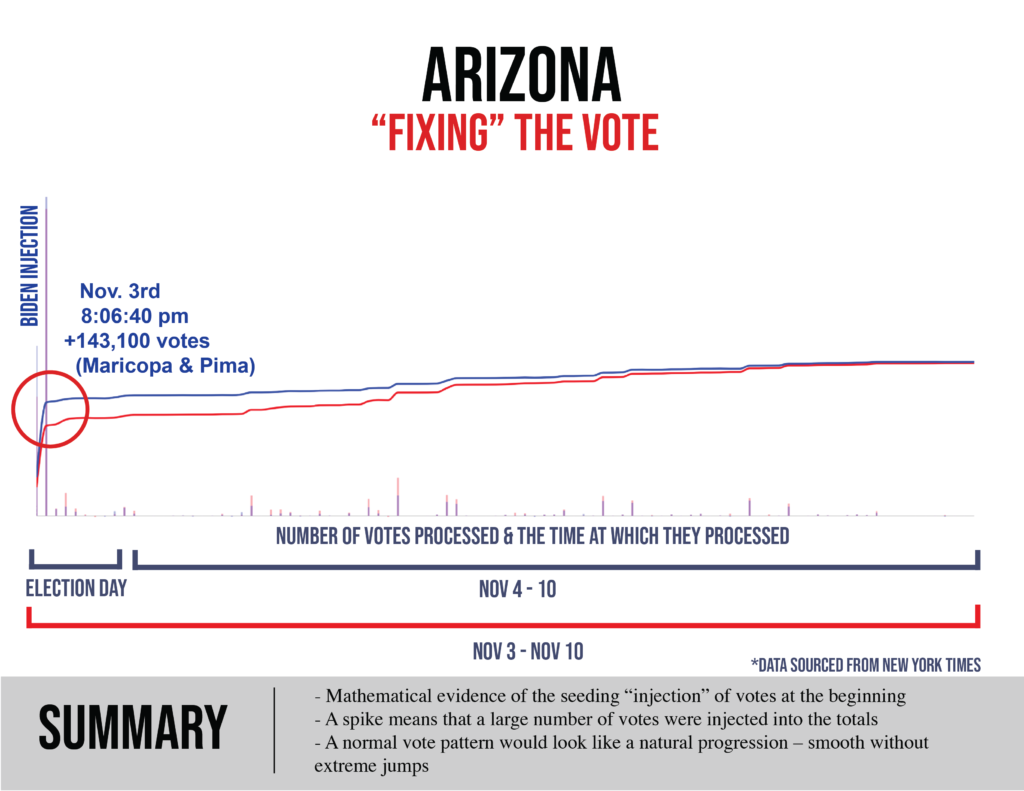
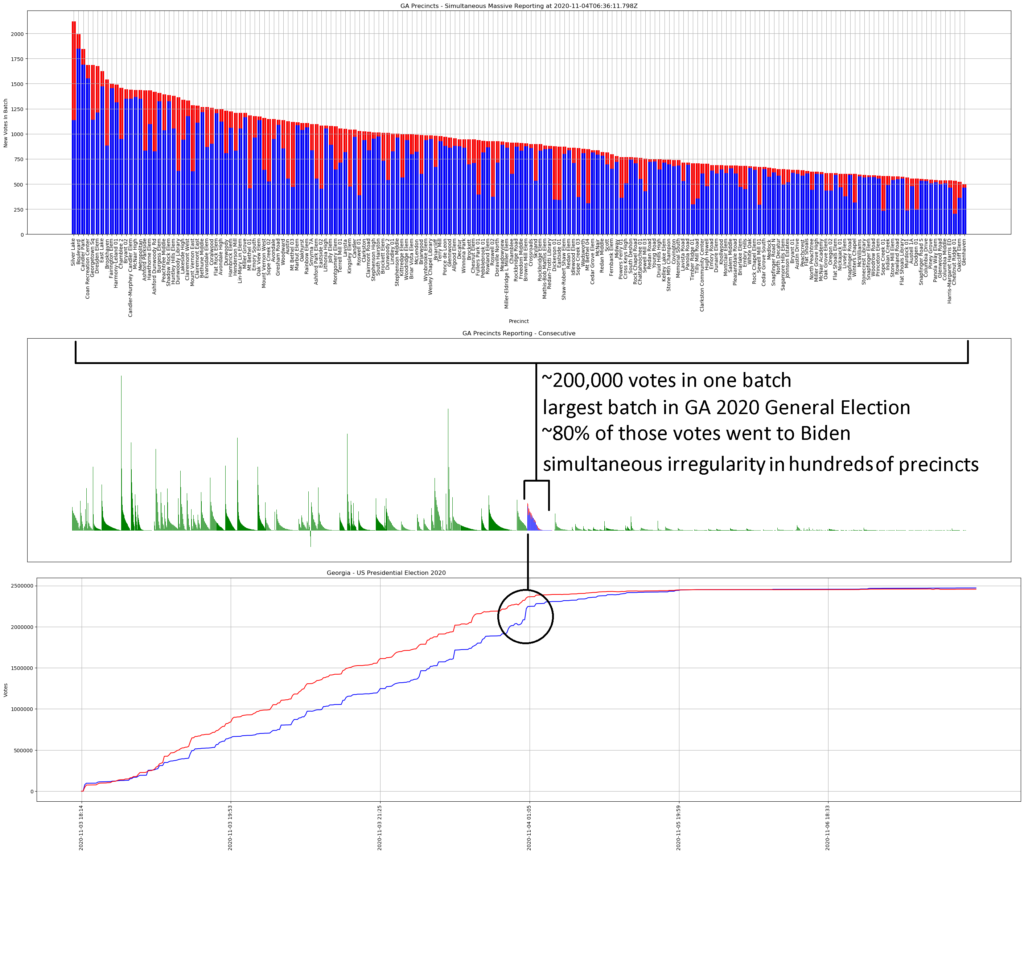
Within a matter of a couple weeks, there were mathematicians publicly and privately weighing in on the statistical improbabilities bubbling up through the November 3 data. Benford’s law, a statistical law frequently used in courts when establishing voter fraud, was applied to the election results in Michigan: “Biden’s vote numbers in Michigan do not match Benford’s law at a 99.999% significance level.“
A Williams math professor laid it on the line (“Yale Trained Mathematician Flags 100,000 Pennsylvania Ballots As Likely Fraudulent“) leading to official reaction (“Federal Elections Commission Chairman Trey Trainor says new analysis by professor Steven Miller ‘adds to the conclusions that some level of voter fraud took place in this year’s election'”).
Before the end of the year noted economist John Lott would come out with a paper: “A Simple Test for the Extent of Vote Fraud with Absentee Ballots in the 2020 Presidential Election: Georgia and Pennsylvania Data“. Lott’s findings were summarized in the popular press, “Expert: Biden win ‘suspicious,’ 289,000 election-changing ‘excess’ votes“.
And so on and so forth.
My purpose is not at this point to convince you, the reader, that election fraud necessarily occurred. My purpose is to convince you that there is a lot about Election 2020 that smells like skunk, enough that it was not and is not reasonable to imagine it should just be swept under the rug. After all, the first lesson we learn in 5th grade civics is that “just law derives from the consent of the governed,” and how we find out what it is to which the governed, in fact, consent, is to hold elections that are free, fair, and transparent. It is the most atomic concept of our intellectual tradition. And in my view any reasonable person who looks at that preceding constellation of facts will say, “There is enough mischief that we need to dig deeper.” And any who look at the preceding constellation of facts and articles and videos and data and says, “Nope, I don’t spot anything there that suggests further examination,” is gas-lighting.
Now I am going to skip ahead a moment, and address what it is that I thought should be done. I am going to do that now so as not to leave the reader in suspense, and so that the reader might accurately job the course of action and choose to take, nad decisions i made along the way.
What is it I thought should be done? Clearly we were dancing among many a Constitutional live wire, I knew, but by the middle of November the election was to me an egg that might not be able to be unscrambled. The following seemed to me as reasonable, unobjectionable course of action as one could take, and least injurious to the Constitution:
Let’s look at the five counties where oddities occurred. These machines were sold to the public with the promise that “there is always a paper ballot as a fail-safe”. Lets hold them to it. Open up the boxes with all the paper ballots and count them, on live-stream TV. Use the US Marshal Service, or use the National Guard (“Our sons and daughters and co-workers…. Our Citizen Soldiers”). If there are not big discrepancies, then Trump concedes. But if there are big discrepancies, we still are not going to ask the Courts to simply give Trump the win. Instead, we would rerun the election in those five states, using, again, the National Guard and the US Marshall service. Yes it would be a bad precedent, but so would trying to force down the public’s throat an election that was rumbled by goons in five key cities, and about which between 33% – 47% of the population has significant doubts. That’s not healthy for democracy, either. I figured the initial read of the ballots in five counties would take 2-3 days, and if the election were rerun in those five states, in 30 days. Easy.
Which is why in early-mid November, I was hoping that brisk action would be taken. The results would create a world where President Trump would either say, “See, there were discrepancies in the hundreds of thousands of votes in each of these locations. We are re-rerunning the election in those five states using the National Guard.” Or he would say, “No big discrepancies, fine I concede”. If undertaken with dispatch, the entire matter might have been resolved in about three days; if discrepencies appeared, the rerun of the election might even have been resolved in time for normal operation of the Electoral College on December 14.
That’s it. That was the plan. It went through various elaborations, various nice-to-haves, but at heart that is all that was sought by myself and the team of Bad News Bears that had found each other. That is all that was needed. The alternative was accepting a highly irregular national election that would divide our nation for years. That is why I say, “This was a 3-foot putt. Maybe easier.” Seems rather tame and reasonable to me (though i suspect we are entering an era where the thought-control goons will label the plan I just described as, “extremist”).
Now I know from experience there are those who will say coyly, “But how do you know that cheating occurred?” We don’t, fully: what we know is that five cities play a special role in US political science because of their ability to flip five key swing states; those five cities saw bizarre and unprecedented activity on voting night, up to and including the shutting down of vote counting (the water pipes knew just which cities in which to break?); in each case a huge spike of Biden votes were injected where counting had ceased and observers had been cut out. Personally, I think it is brazen enough that I take it as an insult to my intelligence to be asked to accept that there is nothing to this fact-pattern, without investigation.
But in my view the test is not, “Is there enough sketchy information available that we can be sure that election fraud occurred on a scale that changed the national election?” Rather, the test was, “Does this smell enough like skunk that we should just open up the boxes with all the paper ballot backups, and recount the whole thing on livestream TV? After all, there is a reason the machines were sold to us as always having the paper ballots as a fail-safe: if there were ever a time to use it, now would be that time.”
Yet I get ahead of myself. I have filled you in, Dear Reader, on how I read the evidence, what it suggested to me, and the course I tried to hip-check our country into taking (whene’er a chance I got) as the weeks and ultimately following two months unfolded, up until January 6. So you know where I am coming from in the story that follows: those were the grounds of my suspicions and the course of action I thought should be taken to minimize injury to the Constitution while doing our best to unscramble an election that had become hopelessly compromised.
But now let us go back to November 4, the day after the election, when the whole country began grappling with a question that our little team of Bad News Bears had been working on for months.
Within days a self-organized digital army sprung into existence. Networks of volunteers. People willing to research any question we needed answered, anywhere in the country; people willing to track down others and record their experiences; precinct voters who had experienced some of the techniques of the fraud first-hand, at a retail level; precinct workers describing extraordinarily lax enforcement of standards; freight drivers who had realized they were moving hundreds of thousands of fake ballots from one state to another. Lawyers who were able to mobilize, research local laws, and gather sworn statements. It quickly became clear that the problem was not going to be turning up facts, it was going to be managing the fire-hose of facts that were pouring in. More and more Americans were stepping forward with details of things they had experienced or witnessed on Election Day. These networks began finding each other then finding me, and I helped out in places where I could, as I pulled together a team of people who could handle such a flow of information. The cyber team collecting and processing data, the affidavits coming in by the dozens, then hundreds, and then thousands (ultimately I heard that 50,000 Americans signed affidavits concerning their experiences).
Because of our preparation we had more than a rough idea how the various frauds had occurred, in various permutations, on retail, wholesale, and industrial scales, in the different states in question. We knew that nailing things down for the benefit of a court of law someday might require examining hard drives and performing other computer forensics, but (as I walked through in the paragraphs above) the rough outline of the steal was child’s play to see. The mountains of new statements and affidavits and data that surfaced daily further confirmed that larger theory (for example, the odd “Sharpie switcheroo” of Phoenix-Maricopa county became explicable when one understands that ballots poorly read by the machines become fodder for mass “adjudication” of which we had confirmed the machines were capable).
By a week after the election the cyber-sleuths and investigators with me already had things perhaps 50% sorted out. They had the strategy behind the theft: pick those five cities to cheat like hell, flip their states, thus flip the electoral college and the nation. More refined versions of the strategy evolved over subsequent weeks (we found, for example, that whoever was doing the stealing in Georgia also targeted heavily red counties and shaved a few percentage points in each). Statistical outliers were showing up of astronomical unlikelihood, rivers of affidavits were gushing in where people reported experiences precisely consistent with what our team had predicted was happening under the hood of the steal, and so on and so forth.
Mathematicians began contacting us with analyses that confirmed what we were putting together empirically, only a fraction of which made it into the press (“MIT statistician shows certainty of massive computer vote fraud in 2020 Presidential election: Dr. Shiva Ayyadurai (Dr. Shiva) provides an MIT PhD analysis of Michigan voting patterns….“)
An excellent quant (Seth Keshel) who joined our team went on to give a rather dense analysis to the public on January 1, but in truth everything he says here is what was already bubbling up among us by mid-November. For those who want to see a good quantitative explanation with data and maps, watch this 20 minutes:

Approximately one week after the election I walked into an office building in suburban Virginia, just outside DC. That is to say, a week after November 3, my colleagues and cyber experts walked in with a still-fragmentary yet compelling reconstruction of what had happened on November 3 and the days immediately following it. We had the crime about half-solved, and what was remaining seemed almost a mechanical matter: dig here, compare this with that, see what answers spit out. We can see they were doing this this and this, but we also need to look into that.
I and my cyber-sleuth colleagues walked into that building to take a meeting with America’s Mayor, Rudy Giuliani, and with Sidney Powell, Esq. (esteemed lawyer for Michael Flynn, the “Peoples’ General”).
And that, dear reader, is where our story really begins.
Subscribe to our evening newsletter to stay informed during these challenging times!!
Sure it is not RS-232 instead of r232? Also soldering slots might cause the board to malfunction. Disabling them might be better
I enjoyed this article and very much look forward to the next installment.
Mark Smith, if you would have read his story you would have noticed he had indicated that there were a few mistakes due to his needing to get this info out and that he would clean it up later. Hence the r232 vs the RS232. Lets pay attention to the real substance of the story shall we.
Excellent article.
Now, what is the action plan for 2022?
We need one or two people working full-time following the events in all the targeted states (CA, TX, NM, AZ, GA, FL, PA, MI, WI, ?) who collate, track, and report to us once a week.
Based on what happens with these states and changes to their laws, we then need a couple of people to formulate anti-election fraud tactics and organizing groups in each state to insure election integrity.
Questions that need to be answered include:
- What do we do if observers are not allowed to see ballots again? Or objections ignored? Or are kicked out without cause?
Observers need to be within three feet of the actual ballots, and need their objections heard, but I'm not seeing this addressed in law as of yet? (it's still early)
But if we can't get the election laws and processes repaired, does it only leave us with massive "peaceful" sit-ins? Do we need 10K volunteers to be ready in each city to go where the illegality is occurring with large signs ready to sit in and go to jail? Do we also need our own citizen media crew with multiple livestreams running, and real cameras with telephoto lenses?
- What do we do to get dead, underaged, and out of state voters off the voter roles, and stop universal mail-in ballots without protections?
If we can't get these people scrubbed, do we just let the other side use them again to steel another election?
This is going to sound sad, but if this is NOT fixed is the only option to preemptively vote for them before the cheaters do? I do not like this option, but if they refuse to take these people off the voter rolls so they can illegally using them again, is our only hope to beat them to the punch? If we have to stoop to their level, maybe we insure each candidate gets the same number of votes insuring all the fake ballots have zero effect on the election?
- What do we do about the insecure machines used in 2020?
You know, before we develop a plan for 2022 we need to push to get the laws and processes fixed in 2021 - the more we know the updated laws, the better we can plan to expose any fraud in 2022.
Michael7