
Editor's Note - We are not saying that Russia does not interfere in U.S. elections -- they have since the Soviet Union and will continue to do so in the future, as we do in theirs. This article simply relates to the Deep State manufacturing of information against President Trump, and associated actions by the DNC. The article begins after Wikileaks had already received DNC emails, likely downloaded from a thumb drive according to our interview with Bill Binney. The hack described below is a separate issue from that event.
For the last few years, dozens of articles claiming to break the story on the DNC hacks, 2016 election interference, the coup against Donald Trump, or the across-the-board Information Operation (IO) against the Trump presidency have popped up.
I’m not about to knock journalists, or the work they did uncovering parts of what happened at all, because all of it is important and some of it is groundbreaking.
But the reality is I started breaking all these stories in late 2014. I followed their development through the lens of the groups, actors, contractors, US Government officials, and clients who were setting this entire operation up from the time it was in the early stages of brainstorming and strategy building.
Foreign Policy reported I was the early primary source for Donald Trump’s views on Ukraine that sparked the impeachment. MSNBC, CBS, and 60 Minutes came to the same conclusion.
According to 2x NYT Pulitzer Prize winner for stories on the DNC hack and 2016 election interference, Scott Shane, I’m the early, primary original source for the following information -- Clinton, Crowdstrike, Ukraine collusion in the DNC hacks, Trump’s views on Ukrainian interference and:
∙ The DNC, Clinton, Obama-Biden, ODNI, FBI, Ukraine, and Ukrainian Diaspora collusion in the 2016 election interference stories
∙ Election interference including US media, social media blackballing and de-platforming of journalists and media platforms
∙ Blacklisting journalists that began in 2015 and went mainstream with the introduction of fake news
∙ FBI criminally hiding the DNC hacker as part of the Obama administration led IO
∙ The development of the US coup and IO in Ukraine. The events from 2014 Maidan, MH-17 through 2016 were part of that.
∙ The Information Operation in Ukraine morphed into the Information Operation against Donald Trump resulting in his impeachment and the ongoing protests, riots, and Intel community coup attempts
The reason for the attention is the density of primary source information I’ve included in the articles I’ve written. Imagine, a 2x Pulitzer winner can’t argue with the evidence on the very events he won those prizes on.
Now that we’ve established creds, there are only two platforms on the web that have the courage to publish the evidence I present. The first breaking news article about the DNC hack showing the groups involved was at Washingtonsblog.com which was taken down by the same de-platforming, hacking and defunding going on today.
[Preface by Washington’s Blog: As patriotic Americans, we are most concerned about what’s best for the U.S. If it’s Ukrainians – more than Russians – who are interfering with our country, we have a right to know. We are for uncovering the truth, wherever that may lead. As such, we bring you alternative voices and on-the-ground reporting. Then we let you decide what you believe.]
The second is CDMedia (cdm.press). When I told L Todd Wood about what to expect, his reaction was -- if the facts are there we publish. Within a few days of the first article, Twitter suspended 8 of CD Media’s accounts, Paypal and other transfer companies suspended CDMedia accounts, and his LinkedIn profile has just been suspended after the first episode of the video series Information Operation, where we are breaking all of this down.
After all this occurred, right after brushing shoulders with me for the first time, Wood never wavered. His attitude is truth first...if the story is backed with evidence, consequences be damned.
CDMedia will be opening all the detail to these stories in addition to their groundbreaking work on the Biden-Burisma story, Obamagate corruption, and Ukraine’s interference in American politics.
Meet Alice the DNC hacker nobody wants to implicate
Before we get to the big reveal, it’s important to emphasize the Obama-Biden administration, FBI, ODNI, CIA, FBI, Robert Mueller, DNC, Hillary Clinton, Team Clinton, Alexandra Chalupa, the US Embassy in Kiev, the Kerry State Department, the Ukrainian government, Ukrainian Foreign Ministry, Ukrainian Ministry of Information Policy, SCL, IOTA-Global, Cambridge Analytica, the Atlantic Council, Crowdstrike (Alperovitch), Bellingcat, Aaron Weisburd, and a host of DNC related groups knew who the DNC hacker was before the hack allegations began.
What you are about to read clears Julian Assange of receiving the DNC hack material from the Russians and clears the Russian government from responsibility of the hack and 2016 election influence campaign. Because WikiLeaks was the third to publish the leaked DNC files and took no part in their removal, revealing Alice’s identity and the part she played in the DNC hack is the final leg showing there is no case against Assange possible if there was no crime committed against the DNC.
Her hacking nom de guerre is Alice. All her hacking group’s names are based in Lewis Carroll’s In through the Looking Glass. Her real name is Irina Shevchenko. She was born in Ukraine. She lives in Ukraine. She works in Kiev. She is Ukrainian. Shevchenko worked with the Ukrainian government through the Ukrainian Ministry of Information Policy. Irina worked with the Ukrainian SBU.
Irina Shevchenko worked for Alexandra Chalupa’s Oppo Research team for Team Clinton and the DNC and Information Operations implicating the Russian government.
After establishing what Shevchenko was doing and her relationship to the Ukrainian government through the Ukrainian IO teams through primary evidence quotes, I’ll show once again Crowdstrike and Dimitry were working hand in glove with the hackers and developing the Russian influence story.
But the big takeaway from all of this is Hillary Clinton ordered the DNC hack to happen. This one point exonerates Julian Assange from liability for the files WikiLeaks released. She didn’t want Julian Assange or Wikileaks in a position to leak any more information about her “incoming” administration.

Her group, Shaltay Boltay (Humpty Dumpty/Anonymous International) was part of the SCL-IOTAGlobal team put together under the Ukrainian Ministry of Information’s Dimitry Zolotukhin and Christina Dobrovolska. They were part of a larger Ukrainian hacking IO group called Cyber-Hunta with partner group Ukraine Cyber Alliance. These groups were subordinate to the InformNapalm group in Ukraine.
This West Point report shows clearly these groups are Ukrainian Information Operations actors.
“The StopFake project at Kyiv Mohyla and InformNapalm further add to the success of counter-IO operations in Ukraine across all levels.”- DEFENDING THE BORDERLAND Ukrainian Military Experiences with IO, Cyber, and EW By Aaron F. Brantly, Nerea M. Cal and Devlin P. Winkelstein- Army Cyber Institute at West Point
Shevchenko’s group, Shaltay Boltay started building the Russian influence part for SCL in 2014 from Kiev as a part of the InformNapalm group. Robert Mueller’s investigation, all subsequent investigations, media reports, and accusations are based in the Shaltay Boltay fabrication about the Internet Research Agency linked to Russian oligarch Yevgeny Prigozhin and based in Saint Petersburg, Russia influencing the 2016 election.
Shevchenko’s group Shaltay Boltay worked the MH-17 Information Operation which fed the investigators fabricated evidence and shut down any real hope for closure.
InformNapalm UCA (Ukrainian Cyber Alliance) member RUH8 made the following remarks after Shaltay Boltay leader Anikeevleft Kiev and was arrested in Moscow in October 2016. This is important not just because it shows the relationship but even identifies the charges Anikeev was brought up on in Russia.
“Sometimes they get hacking help from their Russian friends, he says. “There are people there who are so angry at their own government that they are risking spy charges and passing information to us,” RUH8 explains.”- Inside The Ukrainian ‘Hacktivist’ Network Cyberbattling The Kremlin-RFERL
For ten years prior to the 2014 Ukrainian coup, the groups that formed into Ukraine’s IO and OSINT team had a working relationship under Shaltay Boltay leader Vladimir Anikeev. The group worked together stealing credit cards and running IO blackmail schemes on businessmen and government officials alike.
Alice aka Irina Shevchenko was the lead hacker of the group.
According to the official story, Alice would go to high-end coffee shops and pretend to be using her laptop. She cloned the devices of the customers around her and passed the information to the Shaltay Boltay boys who would analyze it for incriminating evidence that could be used for blackmail. The data would be sold online for Bitcoins if the victim didn’t comply and Alice would cash it in Kiev.
They identified themselves as Crowdstrike’s Fancy Bear/Cozy Bear in October 2016 when Ukraine’s CyberHunta hacked teammate Shaltay Boltay using what was then Fancy Bear proprietary tools. No one had the tools except Crowdstrike and the Ukrainian Fancy Bear groups
This was done after Shaltay Boltay only released ½ of the Surkov secretary hack files and Anikeev was arrested in Russia. The Fancy Bear hack was noted in En Route with Sednit Part 1: Approaching the Target Version 1.0 • October 2016 by ESET LLC. Two days after the Shaltay Boltay server was hacked, Ukrainian InformNapalm released the 2nd half of the Surkov files to the Atlantic Council for verification.
Ukrainian Fancy Bear exposed themselves to the world.
(Vladimir) Anikeev is believed to be “Lewis”, the spokesperson for Anonymous International. FSB recently decided to confuse the matters by using the discovery on Anikeev’s computer of #SurkovLeaks files, which had been obtained and published by #UCA (Ukrainian Cyber Alliance), and had already been in the public domain. As the speaker for #UCA, I categorically deny any connections between Ukrainian Cyber Alliance and Anonymous International. I will now try to unravel this KGB tangle. According to RUH8 “Shaltai Boltai people post “samples” of letters of influential, but nonpublic people, virtually without comment. And they also offer information for sale. But did any of the allegedly sold correspondences surface anywhere? Why not? Because a complete dump would inflict a tremendous damage on Moscow, whereas the real goal is to pull some strings and rein in a competitor for power.” .-RUH8 InformNapalm
Now we have the Ukrainian Fancy Bear hackers with a Russian criminal team-mate that was charged with treason in Russia. According to the the FSB was able to retrieve Shaltay Boltay’s archive server from Kiev.
All the InformNapalm groups worked as Ukrainian state IO, hackers, and OSINT for SCL from 2014- today. They worked with Ukraine’s SBU which was given over to Pravy Sektor by Valentyn Nalyvaichenko following the 2014 overthrow of Victor Yanukovych and are mostly Pravy Sektor nationalists.
Initial reports out of Russian media tied Mikhailov to a group of hackers in Ukraine and Thailand called Shaltay Boltay, which means Humpty Dumpty. The group is reportedly affiliated with Anonymous, who released damaging documents on high-level Russians in 2014 and the Kremlin alleges that the arrests are related to this act, as Markov told The Daily Beast that Mikhailov: “definitely controlled Shaltay Boltay,” which “cooperated with the Ukrainian SBU [security service], which is the same as working for the CIA; he worked with them, which is obviously treason.”-Paste Magazine
This is the team of credit card thieves Alexandra Chalupa hired to do Oppo research on Donald Trump? If you look back to 2016, the IO machine was almost on hiatus through the election.
Let’s jump ahead for a moment. In December 2017, Shawn Henry, CEO of Crowdstrike while being interviewed by House Intelligence Committee members could not say for sure there was ever evidence that anything was taken during the DNC hack.
The question is why? It’s going to be obvious soon but why hack into the server and not take anything?
At the same time her aides were creating “loyalty scores”, Clinton, “instructed a trusted aide to access the campaign’s server and download the messages sent and received by top staffers. She believed her campaign had failed her-not the other way around-and she wanted ‘to see who was talking to who, who was leaking to who.”-Jonathan Allen and Amy Parnes. Shattered: Inside Hillary Clinton’s Doomed Campaign
Alexandra Chalupa’s Ukrainian cyber team that was doing the Oppo research also doubled as IT professionals for the DNC. This motley team of petty thieves was given state sized tools to play with for SCL’s IO program in Ukraine which was pointed at the US the entire time. Think Vault 7 size tools. Other than Crowdstrike, they are the only group proven to have the Fancy Bear proprietary tools that identify the group.
Hillary Clinton demands the server is accessed and leakers are found. Irina Shevchenko is the best hacker and coder out of the groups and she’s the go-to girl when the Ukrainians need help. It’s either her or the rabid nationalists with the emotional acuity of 10-year-olds that make up the rest of the team. She decides to use the state sized tools she was given because it means a faster turnaround for the answers Clinton wants. Nothing was taken. Irina Shevchenko of Shaltay Boltay/Ukraine’s CyberHunta/InformNapalm/SCL contractor working for Alexandra Chalupa for Team Hillary was doing her job.
She probably billed Hillary and the DNC for the time and trouble the hack took her.
The FBI protected these groups and when interviewing one of the subgroups allegedly offered a US passport, money, an apartment, and work if the interviewee would pin the hack on Donald Trump and Vladimir Putin. Six of the eight servers linked to the hack belong to Shaltay Boltay.
Since we know Crowdstrike had nothing and ramped up the war on Donald Trump we can safely assert the entire episode was to control the election results and the just released CIA documents prove the point.
“If the U.S. government had come out and done what they did in December 2016 [in releasing an intelligence-community assessment on the interference] in July, it would’ve had an even bigger effect,” said Dmitri Alperovitch, the Russian American founder of the cybersecurity firm CrowdStrike, which was brought in by the DNC to analyze the hack.”- the Atlantic
A little over a month ago I was contacted by Yaacov Apelbaum, the CTO at XRVision. From his LinkedIn profile- Holder of 13 U.S. technology patents and published author. Demonstrable expertise in all aspects of cybersecurity, cutting edge R&D, security architecture, and real-time systems. Premium proficiency in intelligence platforms, Big Data and AI-based analytics, and delivery of some of the world’s largest mission critical and high-volume transnational cloud-based solutions.
He contacted me to compare notes on the DNC hack. His trajectory mirrored mine but his source material was from a different angle. He ended up with the same conclusions. It’s a worthwhile read that breaks it down easily.
From the first DNC hack expose article I wrote in January 2017 it’s been clear and documented that Crowdstrike and Alperovitchhad had an ongoing relationship with the DNC hackers.
The following from his article shows how deep Alperovitch’s relationship extends to them.
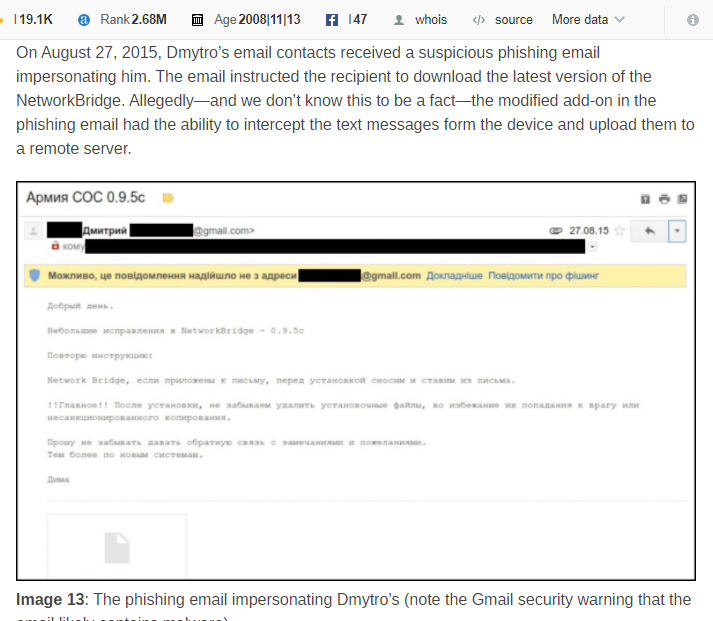
Dmytro immediately told his users not to download the malicious add-on and sent a copy of the phishing email for analysis to a friend, Andriy Baranovych, a Ukrainian hacker that goes by the alias “Sean Townsend”, AKA “Ross Hatefield”, member of “RUH8”. According to Dobronravin and Dmytro, none of their users downloaded the malware because GMail flagged it as suspicious.
Andriy Baranovych, who contracted for Ukrainian intelligence (FSU) and did some work for Alexandra Chalupa/DNC, also just happened to be a friend of Dmitri Alperovitch, the CTO of Crowdstrike and forwarded the code/story to Alperovitch.- Yaacov Apelbaum
So tell me, who hacked the DNC? Was it the Ukrainian Irina Shevchenko?
Or was it the Obama-Biden administration, FBI, ODNI, CIA, FBI, Robert Mueller, DNC, Hillary Clinton, Team Clinton, Alexandra Chalupa, the US Embassy in Kiev, the Kerry State Department, Ukrainian government, Ukrainian Foreign Ministry, Ukrainian Ministry of Information Policy, SCL, IOTA-Global, Cambridge Analytica, the Atlantic Council, Crowdstrike(Alperovitch), Bellingcat, Aaron Weisburd, and a host of DNC related groups?
If Shevchenko can’t be charged for the DNC hack, how can Julian Assange if WikiLeaks was the 3rd in line to publish the DNC leaks?
Subscribe to our evening newsletter to stay informed during these challenging times!!
OMG! What a tangled web of intrigue. Or something. And some of it done with the cooperation of the US intel agencies. Not surprised.
From what I gather from the info, its no wonder the 'Hag' is afraid of the light of day. As she said on '16 election nite, "...we'll all hang if he is elected". Thus the fierce opposition to any investigation into the whole DNC hack and anything else.
The web is even more tangled than I thought.
Thanks for the info. Interesting.
Was Alice at Lou's City Bar in Washington, DC at the same time that Seth Rich was, on the night he was killed, 10 July 2016?
Where does Seth Rich fit in all of this?
A random execution to instill fear among those laboring to install hillary into the White House. It's a tried and proven stalinist tactic designed to keep the nomenklatura in a state of fear.
George, great work I too have been following this line go inquiry since prior to their civil war and the ouster for the friendly Ukraine president to Putin. I assume President Trump is aware if this info....Will any be brought to trial? Hope our President will pardon Julian. Great research you have done. I nominate you for the Nobel. William Joyce...Be safe my friend
Ask Seth about it.
The leak happened before Alice came into the picture. Clinton wanted the server looked at to see who was leaking. Alperovitch used it to create a "hack" not leak scenario and drag WikiLeaks into it.
Seth Rich.
Gee! I guess that you know more about it than Julian Assange! That’s amazing, because Assange has said, more than once, that it was Seth Rich who forwarded the emails to him.
It was two different events. The leak happened and following that Clinton demanded to know who the leaker was by accessing the server. That point is the differential in the equation. The article supports VIPs in its entirety. In fact, if you go to the last paragraph above Alice's photo, you'll find a link that explains it from a previous article.
true story